— Edited:
Part #1: Running Artix Linux as your daily driver
-
- Léo Mercier @Sawangg
Tired of Microsoft shenanigans and Windows eating all of your RAM? In this multiple articles guide you’ll see how to
setup a full disk encryption with Artix Linux and the init system called dinit on your machine as well as rice the
distro to be secure and usefull.
Because we are using Artix Linux, systemd and other common packages found in most Linux distros won’t be included, so it’s going to be more difficult but you will have total control of what package is installed. This article will contain detailed information to guide you through the install process and the next few posts will help you install a graphical interface and more!
Material needed
For this guilde you will need the following
- A USB stick with at least 1GB in storage
- The machine you want to install Artix Linux. This guide was created with a 1TB M2 SSD, AMD CPU and last generation Nvidia GPU in mind but it can be used with any machine, for example I also installed this on a raspberry pi!
- An internet connection
This article was designed so it requires minium effort to follow but you’ll still need the basics (such as exiting vim). Additionally, this guide was done using a french layout keyboard (AZERTY), thus you can skip or modify the sections regarding keyboard mapping.
First step
Download the ISO image on the official Artix Linux website. We will choose the artix-base-dinit-x86_64.iso version to get Artix Linux with dinit. The partitions for our machine will be the following
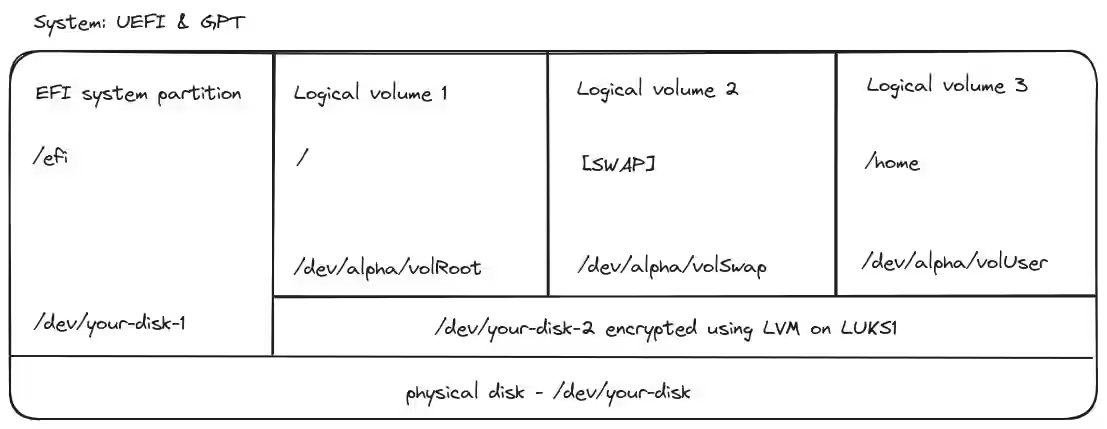
Use this schema as reference if you’re lost with what disk or partitions I use in the commands
This approch is using LVM on LUKS to encrypt our entire system. We will also later on protect our boot/efi partition using the secure bios and an additional tool. This will provide maximum security for our data.
During this guide, I will reference the disk as either /dev/your-disk or a variant of this to indicate a specific partition. You will be able to see if your disk is /dev/sda for a hard drive or /dev/nvme0n1 for an M.2 SSD or any other in the section about wiping your disk.
Create a bootable USB
Locate the ISO you downloaded on your machine and use a tool like dd on Linux or Rufus on Windows to flash the usb.
Here is the command to flash the USB on Linux
dd bs=4M if=path/to/artixlinux-version-x86_64.iso of=/dev/my-usb oflag=direct status=progressOnce the USB is flashed, plug the USB in your PC when it’s shutdown, press the boot menu choice key or change the bootable order in your BIOS and boot onto the USB.
No video output
If you manage to get to the Artix menu, you can skip this small section. If you don’t have any video output, you might need to edit the GRUB boot options. Press e on the Stick/HDD option of the menu and add nomodeset at the end of the line that starts with linux.
linux ... nomodesetPress F10 to boot. You should now have access to the live session menu of your Artix Linux.
Login
You can now login using the default credentials
username: root
password: artixChange your keyboard
Change your keyboard mapping if you didn’t change the keytable in the GRUB options. Here is an example for the AZERTY layout
loadkeys frLogin to the network
We’re going to need an internet connection to download packages further in this guide. If you use an Ethernet cable,
good news, you should already have an up and running internet connection. Depending on what network you’re currently
using, you might also want to change your DNS by editing /etc/resolv.conf and provide a custom DNS server.
Wifi
If you need to connect to a Wifi hotspot, you’re going to use wpa_supplicant provided in the live install of Artix. Run all these commands to connect to your Wifi. You may need to change wlan0 with your interface name that you can find using ip -c addr
rfkill unblock wlan
ip link set wlan0 up
wpa_cli
add_network
set_network 0 ssid "my wifi ssid"
set_network 0 psk "my password"
enable_network 0Wipe your disk
This step ensure that you start with a fresh disk. You can use whatever disk manager tool you’re comfortable with. Be careful if you have data on this drive it will be deleted! You can list your partitions and disks by running:
lsblkWipe the data ⚠️ THIS WILL DELETE ALL THE DATA ON THE SELECTED DISK ⚠️. This can take a long time depending on the size of your disk and your CPU.
dd bs=4096 if=/dev/urandom iflag=nocache of=/dev/your-disk oflag=direct status=progress || trueWAIT for the process to finish and run
syncCreate the Partitions
Now that our disk has been reset to its original state, we’re going to use a tool called parted to create our partitions. Let’s install it
pacman -Syu partedCreate a GPT partition table
parted -s /dev/your-disk mklabel gptWe’re going to use the UEFI & GPT combo. The first partition is going to hold our bootloader and the rest will be encrypted using LVM on LUKS.
parted -s -a optimal /dev/your-disk mkpart "primary" "fat32" "0%" "512MiB"
parted -s /dev/your-disk set 1 esp on
parted -s -a optimal /dev/your-disk mkpart "primary" "ext4" "512MiB" "100%"
parted -s /dev/your-disk set 2 lvm onYou can print the partition table of the drive and see if the alignment of your partition is optimal
lsblk
parted -s /dev/your-disk align-check optimal 1
parted -s /dev/your-disk align-check optimal 2Cryptsetup
Now we’re going to encrypt our disk. To get started run the next command to try to force the unlocking of stronger ciphers
cryptsetup benchmarkIf that didn’t work and you get an N/A on serpent-xts, try rebooting your live environment.
To generate a strong password, you can use this tool: https://rumkin.com/tools/password/
Next we’re going to encrypt the disk using one of the stronger cipher proposed by the benchmark.
cryptsetup --verbose --type luks1 --cipher serpent-xts-plain64 --key-size 512 --hash sha512 --iter-time 10000 --use-random --verify-passphrase luksFormat /dev/your-disk-2Then we mount using the device mapper. A possible reboot here can fix issues mounting the partition.
cryptsetup luksOpen /dev/your-disk-2 alphaLogical & Physical volume
Now it’s possible to create the physical volume
pvcreate /dev/mapper/alphaAnd finally the logical volume that we’ll call alpha
vgcreate alpha /dev/mapper/alphaSystem partitions
Next we can create the 3 partitions needed: swap user and root
lvcreate --contiguous y --size 16G alpha --name volSwap
lvcreate --contiguous y --size 400G alpha --name volUser
lvcreate --contiguous y --extents +100%FREE alpha --name volRootFormat the partitions
We can format each partition to use the correct file system.
mkfs.fat -n ESP -F 32 /dev/your-disk-1
mkswap -L SWAP /dev/alpha/volSwap
mkfs.ext4 -L ROOT /dev/alpha/volRoot
mkfs.ext4 -L HOME /dev/alpha/volUserMount the partitions
We can finally mount our newly created partitions. If you get an error about ext4 being unrecognized, run modprobe ext4 and check if you get an error. If you do, reboot your system and do the following
swapon /dev/alpha/volSwap
mount /dev/alpha/volRoot /mnt
mkdir -p /mnt/boot/efi
mount /dev/your-disk-1 /mnt/boot/efi
mkdir /mnt/home
mount /dev/alpha/volUser /mnt/homeWe did it! We can finally install Artix to our system.
Install Artix
It’s time to install all the necessary packages for your brand new OS.
First we’re going to install the base. I chose dinit but you can use runit openrc or s6 and I also added seatd instead of elogind
basestrap -i /mnt base base-devel dinit seatd seatd-dinit dbus-dinitThen we’re going to chose linux-hardened for more security. We’re going to install more packages like turnstile to fully replace elogind later on.
basestrap -i /mnt linux-firmware linux-hardened linux-hardened-headers mkinitcpio iwd iwd-dinit dhcpcd dhcpcd-dinit openresolv acpi openssh doas man Finally we’re going to install additional packages
basestrap -i /mnt nvim git amd-ucode fastfetchFeel free to replace the amd-ucode with the necessary drivers for your CPU (e.g. intel-ucode). If you are using an Nvidia GPU like I do, I’ll post an article on how to handle the pain that is NVidia on Linux, but this should get you up and running.
Fstab
Generate the fstab
fstabgen -U /mnt >> /mnt/etc/fstabEnsure everything is listed correctly, you should have 4 entries
cat /mnt/etc/fstabIf you’re missing an entry, add it manually, for example this is the command to add your /home
echo -e "# /dev/mapper/alpha-volUser LABEL=HOME\nUUID=`blkid -s UUID -o value /dev/alpha/volUser`\t/home\t\text4\t\trw,relatime\t0 2\n" | tee -a /mnt/etc/fstabOptional
tmpfs is a temporary filesystem that resides in memory or swap partitions. Without systemd, only the /run directory uses tmpfs by default. We can thus reduce the size f the tmpfs partition by using this command
echo -e "\ntmpfs\t\t\t\t\t\t/tmp\t\ttmpfs\t\trw,nosuid,nodev,norelatime,size=8G,mode=1777\t0 0\n" | tee -a /mnt/etc/fstabThe result will be this additional entry in /mnt/etc/fstab
tmpfs /tmp tmpfs rw,nosuid,nodev,norelatime,size=8G,mode=1777 0 0Chroot
Now that we installed the base of our system, we can access it using
artix-chroot /mnt /bin/bashSet your new root password
passwdDoas I do and remove sudo
OpenDoas or doas for short is a portable version of OpenBSD’s doas command, known for being substantially smaller in
size compared to sudo, potentially reducing the attack surface. It is also much easier to configure. For whatever
reason sudo is a dependency of base-devel, we will remove it now
pacman -Rdd sudoTo be extra safe so it can never be installed again, you can edit /etc/pacman.conf and add
IgnorePkg = sudoLocale, Timezone, Host-name and Hosts
First we need to generate our local. If possible, your timezone should be set to UTC and your locale and keymap to
en_US.
echo -e "en_US.UTF-8 UTF-8" >> /etc/locale.gen
locale-gen
echo "LANG=en_US.UTF-8" > /etc/locale.conf
export LANG=en_US.UTF-8Then we need to set our timezone
ln -s /usr/share/zoneinfo/your-continent/your-city /etc/localtime
hwclock --systohcYour system’s hostname is shared with the networks you connect to. You should avoid including identifying terms like your name or operating system in your hostname, instead sticking to generic terms or random strings
echo "Artix" > /etc/hostnameUser account
Next we’re going to create a user account called user
useradd -m user
passwd user
usermod -aG wheel,video,audio,input,storage,power userWe need to enable the use of doas for the wheel group. To do that create /etc/doas.conf and add
permit keepenv :wheelFinally, change the permissions of the file to
chown -c root:root /etc/doas.conf
chmod -c 0400 /etc/doas.confOptional
If you want to persist your password for some time in your terminal after you used it once, you can edit the
doas.conf to this
permit persist keepenv :wheelKeep in mind that this is not as secure as typing your password every time.
Generating the initramfs
pacman -S cryptsetup lvm2 lvm2-dinitnvim /etc/mkinitcpio.confAnd insert encrypt lvm2 and resume between the block and filesystems parameters
HOOKS=(base udev autodetect modconf kms keyboard keymap consolefont block filesystems fsck)Should become
HOOKS=(base udev autodetect modconf kms keyboard keymap consolefont block encrypt lvm2 resume filesystems fsck)Next, we will create a key to decrypt our disk during boot by our bootloader. If we don’t do that, we will be prompted for our encryption key twice instead of one directly on boot. The default path for that key is /crypto_keyfile.bin. BE CAREFUL to never leak this key because it can fully decrypt your disk. We will generate it like this
dd if=/dev/random of=/crypto_keyfile.bin bs=512 count=8 iflag=fullblock
chmod 000 /crypto_keyfile.binAdd the file to the FILES hook of /etc/mkinitcpio.conf and register your key.
sed -i "s/FILES=(/FILES=(\/crypto_keyfile.bin/g" /etc/mkinitcpio.conf
cryptsetup luksAddKey /dev/your-disk-2 /crypto_keyfile.binCompile the image and you’re ready to go
mkinitcpio -p linux-hardenedWe should get a successfull image generation
GRUB
Let’s install GRUB
pacman -S grub efibootmgrRun this command to add the correct configuration. Make sure you reference the correct lvm partition (it should be your second one)
sed -i "s/^GRUB_CMDLINE_LINUX_DEFAULT=.*/GRUB_CMDLINE_LINUX_DEFAULT=\"cryptdevice=UUID=`blkid -s UUID -o value /dev/your-disk-2`:alpha loglevel=3 quiet resume=UUID=`blkid -s UUID -o value /dev/alpha/volSwap` net.iframes=0\"/" /etc/default/grubNext open the file and check if the output of the previous command is correct
nvim /etc/default/grubThen uncomment this line
GRUB_ENABLE_CRYPTODISK="y"Save the file and run the next two commands to install and generate the config
grub-install --target=x86_64-efi --efi-directory=/boot/efi --bootloader-id=artix --recheck /dev/your-disk
grub-mkconfig -o /boot/grub/grub.cfgCheck the output of the command to see if it used our linux-hardened image we created earlier using mkinitcpio.
Boot Time!
It seems like we can now boot into our system.
Exit the termnial, unmount the partitions, shutdown your system, unplug the USB and start it!
exit
umount -R /mnt
swapoff -a
sync
rebootFirst time on the system
Login using your user credentials previously created and enable a few services as ROOT
doas dinitctl enable dbus
doas dinitctl enable lvm2
doas dinitctl enable dhcpcdMachine ID
A unique Machine ID is stored in /var/lib/dbus/machine-id and sometimes in /etc/machine-id. These should be edited
as root (using doas like we did just above) to something generic, such as the Whonix ID:
b08dfa6083e7567a1921a715000001fbDNS
Domain name resolution is a really REALLY important part of your privacy. DNS severs are located in
/etc/resolv.conf which we can manage using the openresolv package. Edit /etc/resolvconf.conf to add your favorite
DNS server that will be used for every network interface regarless of the network configuration.
name_servers=9.9.9.9The end goal here should be to self-host a recursive DNS server like Unbound directly on your machine or on a server
you own instead of using a public DNS server like 9.9.9.9. This is outside of the scope of this article so for now, I
will cover it in a later article.
Brute force
If you REALLY want your DNS to never be overwritten, you can edit /etc/resolv.conf with your favorite DNS server
and run the following to prevent anyone/anything from modifying it
doas chattr +i /etc/resolv.confDHCP
We have to manually enable the DHCP server of iwd. To do so, create /etc/iwd/main.conf and paste this code
[General]
EnableNetworkConfiguration=true
AddressRandomization=network
AddressRandomizationRange=full
[Network]
EnableIPv6=false
NameResolvingService=resolvconf
# OR
NameResolvingService=noneWe’ve enabled MAC spoofing and disabled IPv6 as well as provided openresolv as the DNS manager.
You can start the service, you should get an ip if you’re connected using an Ethernet cable
doas dinitctl enable iwdWifi
You can connect to the wifi by running iwd’s CLI, (change wlan0 if you have a different interface)
iwctl
station wlan0 connect SSIDYou’ve done it!! You have a barebone system with sensible defaults. I hope you enjoyed this long guide and see you in part 2!